Cyber security is utterly critical today, with data breaches becoming more common and sophisticated. As a result, cyber security risk management is a complex and ever-changing field.
After checking out some online surveys, we found around 304.7 million ransomware attempts in the first half of 2021. In the second half, it was even worse, reaching 318.6 million. These figures have even beaten 2020 in total, which was 281.9 million ransomware attacks.
So, it’s apparent that cybersecurity risk management process is complex and requires IT security professionals to understand the threats posed by cyber criminals.
But before this, companies should also understand the concept of cybersecurity risk management, the assessment process, some common threats, plus the best practices to keep their data and resources safe from potential cyber attacks.
What is Cyber Security Risk Management?
Cybersecurity risk management is identifying, assessing, and mitigating risks to an organization’s electronic information and systems. It includes the implementation of security controls to protect against cyber threats. The goal of cyber security risk management is to reduce the probability and impact of cyber attacks. It is a continuous process that should be adapted as the threats develop.
What is a Cyber security Risk Assessment?
A cyber security risk assessment comprehensively evaluates an organization’s cybersecurity risks. It identifies and assesses the risks to the confidentiality, integrity, and availability of electronic information and systems.
The assessment process includes:
- Identifying the assets at risk.
- Assessing the vulnerabilities.
- Determining the impact of a potential breach.
It is important to note that a risk assessment is not a one-time event. It should be performed regularly to ensure that the security controls are adequate and up-to-date.
What are Cyber Threats?
Cyber threats are malicious attacks that exploit vulnerabilities in electronic information and systems. The attackers can gain access to sensitive data, disrupt business operations, or cause damage to the system. There are many different cyber threats like adversarial threats, technical vulnerabilities, and insider threats.
Let’s understand some of the common cyber threats in detail:
- Adversarial Threats: Adversarial threats are the most common type of cyber threat. Cyber criminals who want to gain access to sensitive data or disrupt business operations launch them.
- Technical Vulnerabilities: Technical vulnerabilities are weaknesses in designing or implementing electronic information and systems. Attackers can exploit them to access sensitive data or disrupt business operations.
- Insider Threats: Insider threats are launched by employees, contractors, or other insiders who have legitimate access to the organization’s electronic information and systems. They can exploit their access to gain unauthorised access to sensitive data or disrupt business operations.
Also, know the key threat factors that affect the majority of organisations:
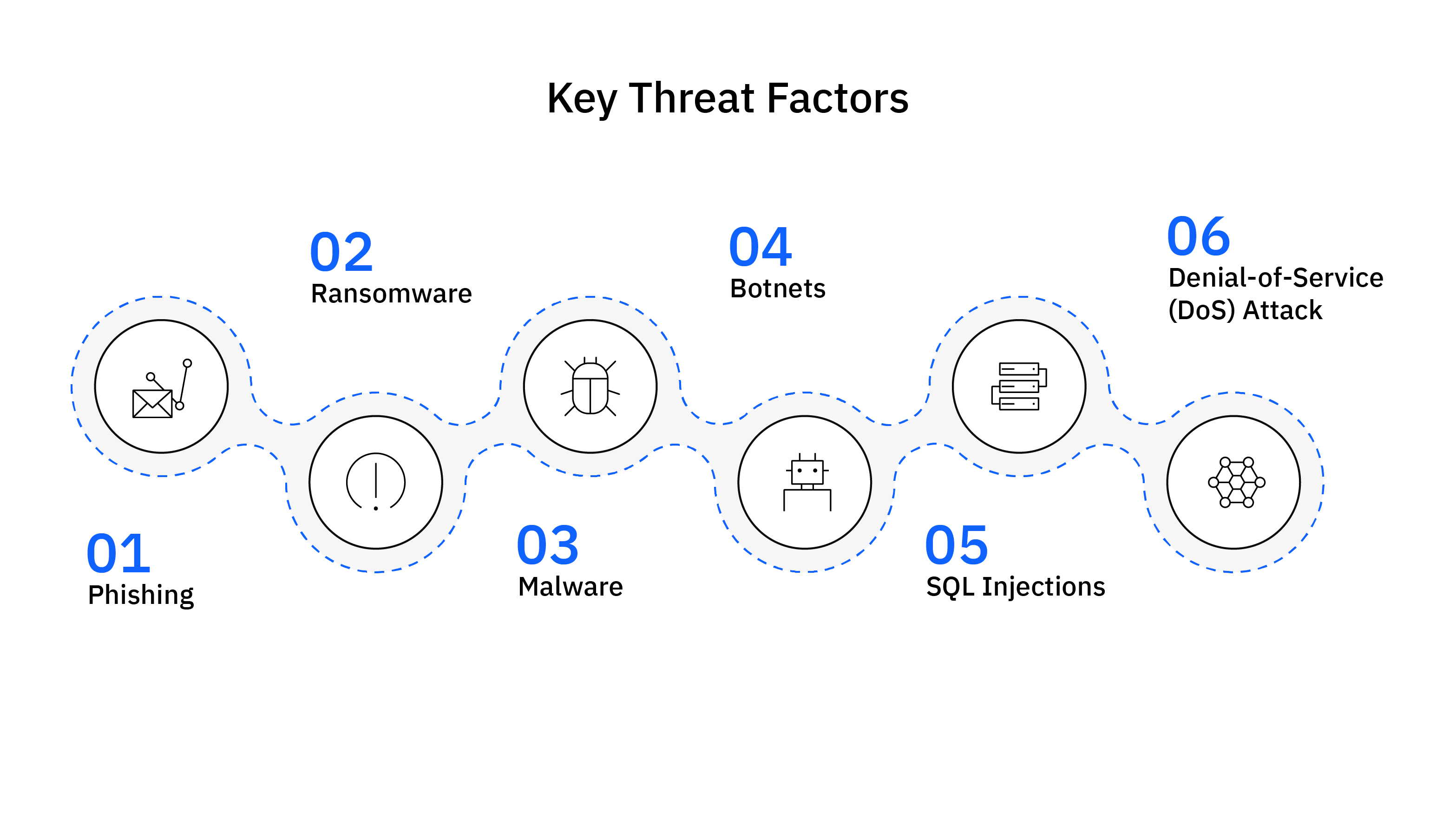
- Phishing: Phishing is a type of cyber-attack that uses email or other forms of communication to trick users into revealing sensitive information or downloading malware.
- Ransomware: A malware that encrypts a victim’s files and demands a ransom to decrypt them.
- Malware: A software designed to damage or disable computers and computer systems.
- Botnets: A network of infected computers that are controlled by a cybercriminal.
- SQL Injection: An attack that inserts malicious code into a database.
- Denial-of-Service (DoS) Attack: An attack that overloads a system with requests, making it unavailable to legitimate users.
Best Practices for Cyber Security Risk Assessment
Here are some best practices for conducting a cyber security risk assessment:
- Identify the Assets at Risk: The first step is to identify the electronic information and systems that need to be protected. It includes all the devices, data, and applications essential to the business’s operation.
- Assess the Vulnerabilities: The next step is to assess the risk based vulnerabilities. It includes identifying the weaknesses in the security controls that attackers could exploit.
- Determine the Impact of a Potential Breach: Always consider the potential impact when conducting a risk assessment. It includes the financial, reputational, and operational damage that a successful attack could cause.
- Perform the Assessment Regularly: The risk assessment should be performed regularly to ensure that the security controls are adequate and up-to-date.
- Use a Tool to Automate the Assessment: Many tools available can automate the risk assessment process. It can help save time and resources.
- Document the Findings: Always document the risk assessment findings. It will help in identifying the risks and implementing appropriate controls.
- Communicate the Results: The risk assessment results should be communicated to all the stakeholders. This will help make informed decisions about the organization’s cyber security posture.
- Review & Update the Security Controls: The security controls should be reviewed and updated regularly to ensure effectiveness. It is also important to test the controls to ensure they are working as intended.
- Train Employees: Employees are also a vital part of the security controls. They should be trained on how to identify and report potential threats.
Cyber Security Risk Management Frameworks
Many different frameworks can be used for managing cyber risk. The following are some of the most common:
- NIST Cybersecurity Framework: The National Institute of Standards and Technology (NIST) Cybersecurity Framework is a set of guidelines for protecting electronic information and systems. It provides a common language for discussing cybersecurity risks.
- ISO 27001: The International Organization for Standardization (ISO) 27001 is a standard for information security management. It offers a certified set of standards that can be used to manage cyber risks.
- DoD RMF: The Department of Defense (DoD) Risk Management Framework (RMF) is a set of guidelines for assessing and managing risks to information systems. It is used by the military and other organizations that handle sensitive data.
- CSF: The Cybersecurity Framework (CSF) is a set of best practices for managing cybersecurity risks. The National Institute of Standards and Technology (NIST) developed it.
- FAIR Framework: The Factor Analysis of Information Risk (FAIR) framework is a set of guidelines for assessing risk. It helps organizations understand, quantify, and manage cyber threats.
Cyber Security Risk Management with Strobes VM365
Strobes VM365 is a risk-centered vulnerability management platform built with the goal of making vulnerability management easier and more efficient. Strobes VM365 is the frontier that gives you the consolidated view of all the findings from various security sources, enabling your teams to focus on resolving the right set of findings. The platform provides a lot of useful features.
The platform allows you to:
- Aggregate all the vulnerabilities from various security scanners, compensatory tools, internal security team, cyber security vendors and bug bounty platforms.
- Auto de-duplicate vulnerabilities of similar nature to ease the burden of doing VM from your IT, Dev & Security teams.
- Prioritize vulnerabilities based on various business metrics and threat intel to narrow down your focus to the top 3% of most risky vulnerabilities.
- Automate your application, network, cloud and container security using no-code workflows.
- Quantify and visualize your organization risk or build your own KRIs & KPIs to enhance visibility for your management.
Watch the Video: Strobes VM365 Demo
Conclusion
We hope you might now understand the importance of conducting a cyber security risk assessment well. Always remember that managing cyber security risks is not child’s play. It is a continuous and comprehensive process that needs to be performed regularly.
There are various frameworks and tools available that can help you manage the risks. Select the one that best suits your organisation’s needs. And, don’t forget to train your employees. They are also a crucial part of the security controls.
Finally, if you are looking for a tool to automate your cyber security risk management process, we recommend you book a demo with us.
Related Reads:
- How CTEM Impacts Cyber Security Insurance Premiums?
- The Critical Risk of Using Dummy Email Domains in Payment Gateways
- Cybersecurity Budgets Set to Grow by 9%: What It Means for Companies?
- Top 13 Cybersecurity Companies in the USA in 2024
- Bridging the Gap: Connecting Cybersecurity Spending to Business Results
- Cybersecurity Trends 2024: Lessons from 2023 & Predictions to Watch Out for!
- New York State Cybersecurity Regulations Now in Effect: What You Need to Know?








