Digital transformation spawns numerous opportunities for growth and value creation across industries. However, rapid digital transformation across businesses also gives rise to digital vulnerabilities that threaten systems.
With the constant development of new technologies like AI, machine learning, IoT, cloud, and big data, threats are constantly evolving and becoming more complex. This increases the requirement for CISO’s and security teams to manage digital transformation risks by augmenting and enhancing their IT and cyber risk management functions.
What are the hidden risks for which most organizations are most vulnerable?
Digital transformation Risks Areas in an Organization
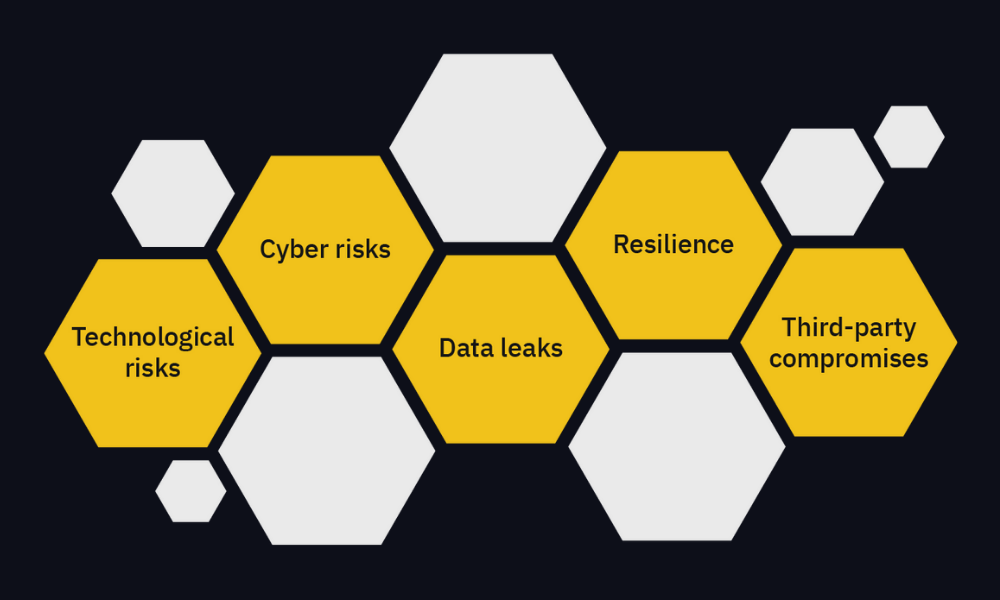
Various internal and third-party factors pose a number of security risks to organizations. Some of the most common include :
Technological risks
This includes potential data loss due to technical issues or obsolete technologies that affect systems, people, and processes. Key risk areas include scalability, compatibility, data duplication, and discrepancies that lead to other organizational errors.
Cyber risks
The internet exposes all systems (including LANs and WANs) to cyber risks, including data breaches using backdoors, Trojan horses, etc. Key risk areas include network security issues, database security issues (backend), and web-application infrastructure security issues.
Data leaks
Ensuring data protection across the digital system is crucial at all stages of the data life cycle. Attacks like the infamous Solarwinds scandal (link to article) can leave even big businesses reeling under the pressure of both legal and organizational consequences. Key risk areas include data classification, data retention, data processing, and data encryption.
Resilience
High dependency on tightly-coupled software can result in services downtime and operational disruptions. For example, if all computers on a LAN are connected to one server node (Star network topology), an attack on the server potentially threatens the entire system. Key risk areas include disruption in business continuity, IT/network disaster recovery, cyber resiliency, and crisis management.
Third-party compromises
Digital transformation risks can arise due to inappropriate controls during vendor or third-party operating processes. This is a direct result of the ambiguity of the risk landscape related to any full-scale business sector. Key areas include data sharing, technology integration, operations dependency, vendor resiliency, etc.
Navigating Digital Transformation Risks
Strobes is vendor agnostic, one-stop shop that caters to all your security needs. We understand the importance of prevention and fix, and work towards countering active threats and mitigating possible risks. Our platform can help you with:
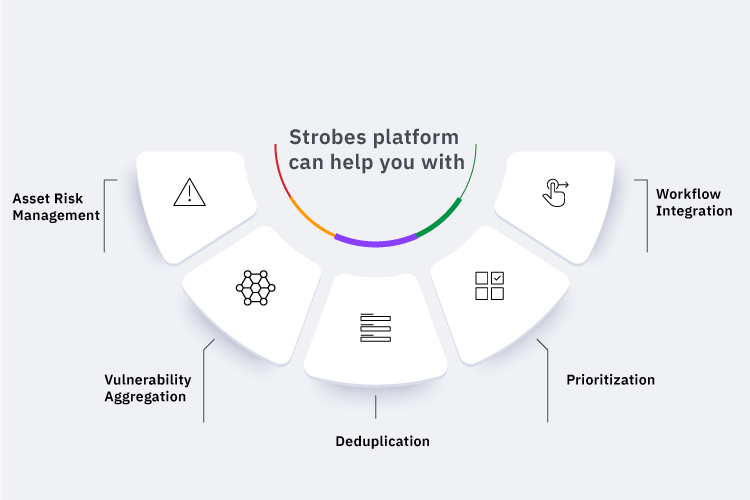
Asset Risk Management
Whether it’s your web application, mobile app, API, cloud instance, host, or network component, you can onboard each of your investments on Strobes and ensure a 360-degree security overview. We help you onboard multiple teams like security, DevOps, and IT, so everyone has access to a single, comprehensive risk management platform.
Vulnerability Aggregation
Ingress vulnerabilities from a new source shouldn’t be a scary proposition for your teams. Strobes comes with native open-source scanners to give you a head start. Our platform allows you to bring commercial scanners, internal security teams, external vendor reports, bug bounties, and every other security source you own into play without having to worry about multiple outputs.
Deduplication
Dreadfully mundane tasks like deduplication drain the analyst’s energy and focus. Strobes ensures all purely administrative tasks like these are handled automatically through high-power ML programs that are capable of detecting and solving deduplication errors within seconds. This helps your top analysts focus on more important tasks that help the organization move forward.
Prioritization
Digital transformation risks can’t be tackled on a first-come-first-serve basis. Each risk brings with it a number of consequences – each of which needs to be tackled in terms of their impact on the company. Our platform includes an ingenious vulnerability priority scoring system that lets you know which risk to prioritize. The prioritization score computes the impact based on eight comprehensive parameters such as business sensitivity, asset exposure, etc.
Workflow Integration
The lack of integration between different parts of your vulnerability management workflow can lead to inefficiencies and clusters of overlapping information. Strobes integrates with various open-source tools such as DAST, SAST, and Cloud, enabling you to increase productivity. We give you a single platform to monitor and mitigate vulnerabilities across all assets.
Conclusion
Digital transformation has resulted in rapidly changing business environments that offer countless opportunities for innovation. With innovation, there will be additional digital transformation risks.
Strobes is a one-stop solution for all security stakeholders, ensuring that the business is well-guarded against technical issues and security threats. Whether it’s your web application, mobile app, API, cloud instance, host, or network component, Strobes supports your investments, acting as an all-round security solution that ensures comprehensive digital transformation risks mitigation.
With the visibility to view all risks for each asset in the dashboard to supporting integrations with leading scanners and bug bounty tools, Strobes provides you and your organisation complete 360-degree protection. See how Strobes can simplify risk management, book your free demo today.
Related Reads:
- Rise in the need of VM platforms
- What is Vulnerability Management? Compliance, Challenges, & Solutions
- How Strobes Uses CASM Security to Uncover Hidden Cloud Risks
- Strobes Custom Dashboards: Redefining Risk-Based Vulnerability Management
- Demystify the Cyber Security Risk Management
- Solution: Risk Based Vulnerability Management