In an era where businesses increasingly rely on cloud services to store, manage, and process critical data, security is paramount. Are you confident that your cloud infrastructure can withstand sophisticated cyber threats? Don’t leave your cloud environment vulnerable to attacks; secure it with our Cloud Pentesting services.
AWS Pentesting
- Whether you are migrating data to AWS, developing applications, or annual pentesting for compliance, AWS pentesting is vital for identifying cloud security gaps.
- Strobes identifies vulnerabilities, credentials, and misconfigurations during AWS pentesting.
- Our expert cloud pentesters use findings to access restricted resources, elevate user privileges, and expose sensitive data, including internet-exposed interfaces and S3 buckets.
Azure Pentesting
- Microsoft Azure penetration testing ensures the security of your cloud infrastructure is maintained while migrating to Azure, developing applications, or during pentesting for compliance.
- Strobes identifies high-impact vulnerabilities in your Azure cloud services, including applications exposed to the internet.
- Strobes Azure pentesting uncovers credentials, excessive privileges, and misconfigurations in Azure Active Directory, preventing compromise and data exposure.
GCP Pentesting
- Essential for organizations migrating to Google Cloud, developing applications in GCP, or using Google Kubernetes Engine (GKE).
- Strobes conducts Google Cloud pentesting for vulnerabilities exploitable by adversaries.
- Manual exploitation of vulnerabilities and misconfigurations goes beyond automated scanning, revealing security gaps in your Google Cloud attack surface.
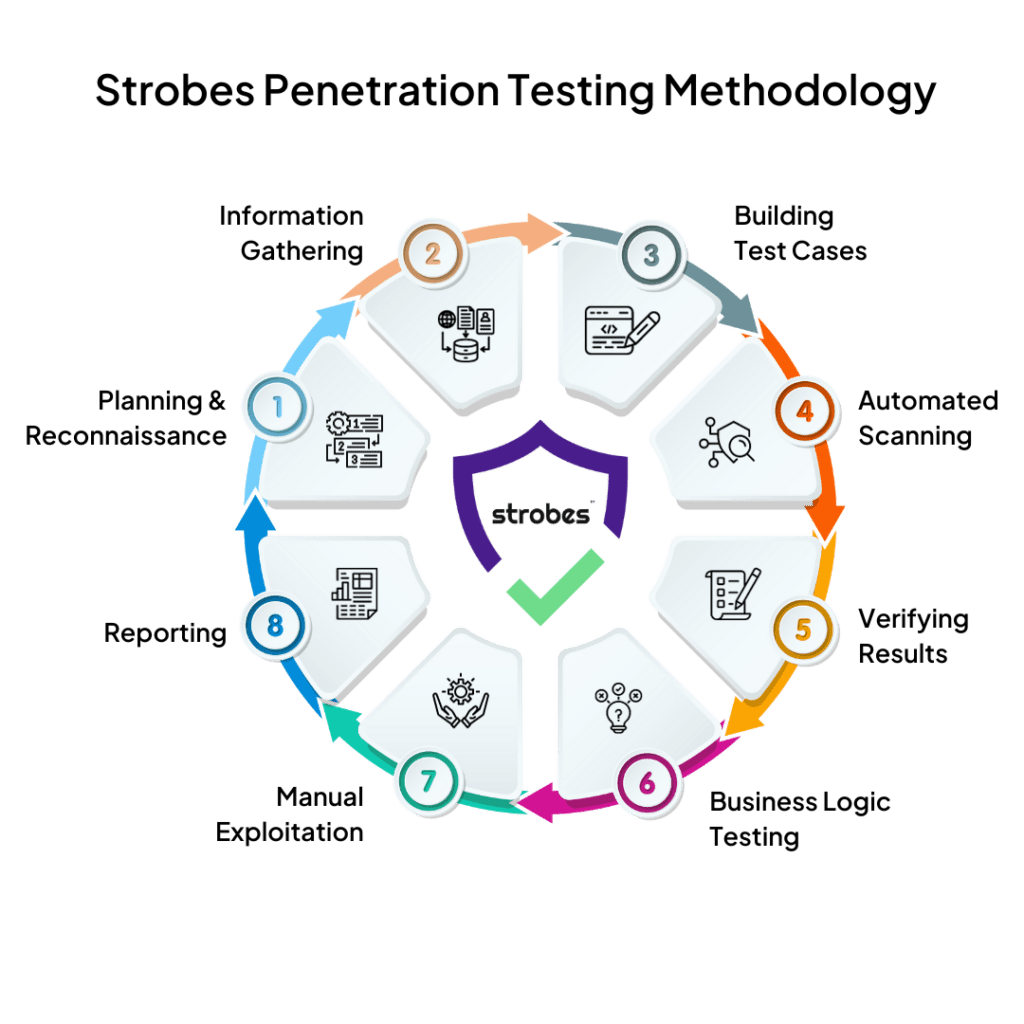
The Methodology
Best at customer support
Multiple reports for your needs
We offer an array of meticulously crafted reports that cater to diverse stakeholders, ensuring everyone stays in the loop with a clear understanding of your application’s security.
Executive Summary Report
Technical Report
Remediation Report
Compliance Report
Business Impact Analysis
Recommendations and Best Practices
Where Automation Meets Human Brilliance
Your success is our priority, and we believe that achieving it should never be a compromise between automation and human touch. With Strobes, you get the best of both worlds, ensuring that every decision you make is guided by efficiency and expertise. Say goodbye to inefficient manual reviews as we lead the way to a future where you can save time and resources, with up to an 80% reduction in manual processes.