In today’s digital landscape, the question isn’t whether, but when, you’ll be targeted by cyber threats. With Assumed Breach, we embrace a proactive cybersecurity approach that operates under the assumption that a breach is inevitable. It’s not a matter of if, but how well-prepared you are to respond.
Tailored to Your Organization's Maturity
Internal View
Insider Threat Perspective
We adopt the viewpoint of an insider with legitimate access to your systems, assessing vulnerabilities and potential misuse of privileges from within.
Red vs Blue
Testing Blue Team Effectiveness
We evaluate the efficiency of your internal security team (blue team) by simulating real-world attacks and analyzing their response.
Lateral Moment
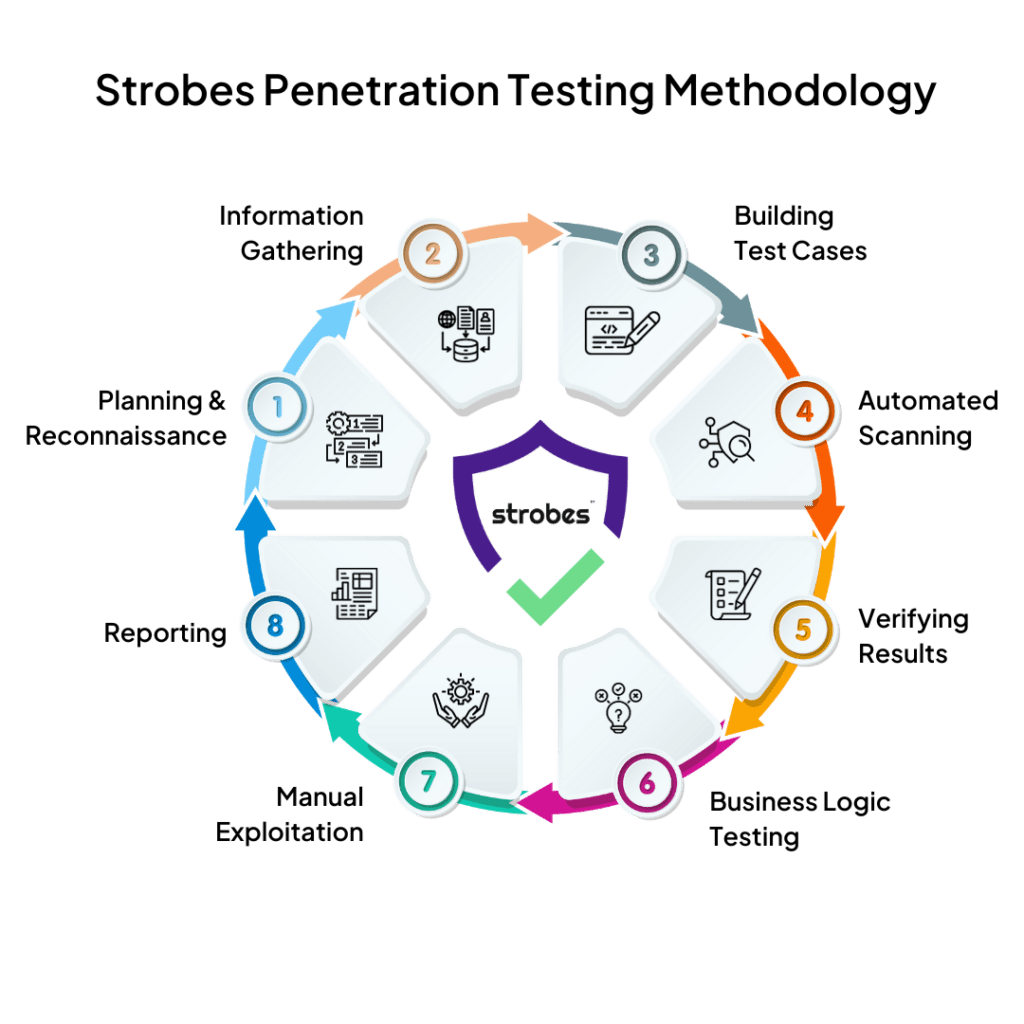
The Methodology
Best at customer support
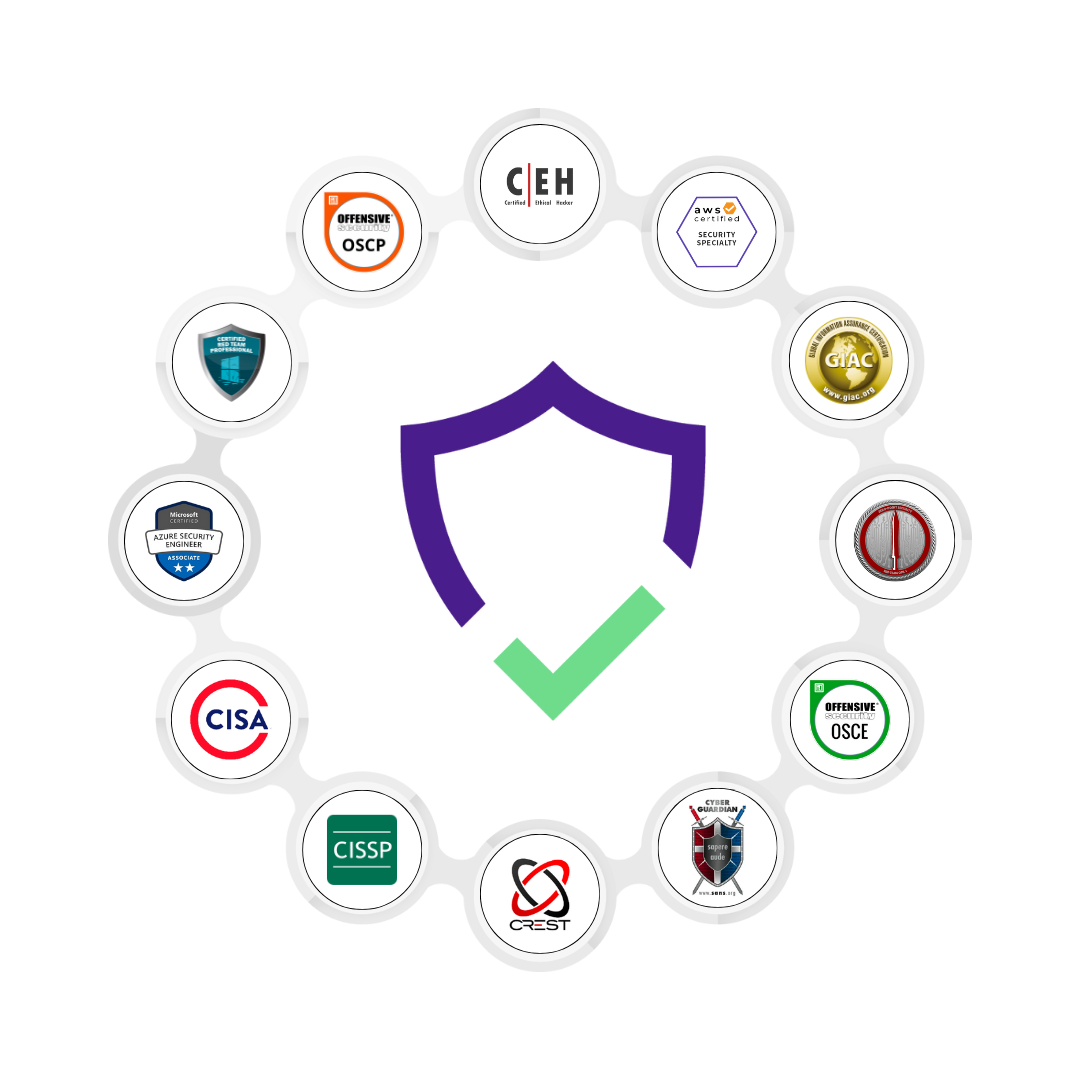
Certified Ethical Hackers
Recognized by certifications such as CREST, OSCP, CISSP, and CEH, our experts are the backbone of our commitment to unparalleled security standards
Multiple reports for your needs
We offer an array of meticulously crafted reports that cater to diverse stakeholders, ensuring everyone stays in the loop with a clear understanding of your application’s security.
Executive Summary Report
Technical Report
Remediation Report
Compliance Report
Business Impact Analysis
Recommendations and Best Practices

Penetration Testing Requirements Covered by Strobes
At the core of our unwavering dedication to top-tier security standards are our certified experts. Embodying excellence through prestigious certifications like CREST, OSCP, CISSP, and CEH, our team stands as the bedrock of unparalleled security expertise.
Where Automation Meets Human Brilliance
Your success is our priority, and we believe that achieving it should never be a compromise between automation and human touch. With Strobes, you get the best of both worlds, ensuring that every decision you make is guided by efficiency and expertise. Say goodbye to inefficient manual reviews as we lead the way to a future where you can save time and resources, with up to an 80% reduction in manual processes.