Strobes is an integrated cybersecurity platform that combines Attack Surface Management, Penetration Testing-as-a-service, and Risk-Based Vulnerability Management to continuously manage your threat exposure.
Choose Strobes As Your Continuous Threat Exposure Partner
Strobes is among the world's first cybersecurity platforms specifically designed for end-to-end continuous threat exposure management. This ensures that organizations are equipped with cutting-edge tools and methodologies to address evolving cyber threats.
Pioneering Platform
Charting Your Continuous Threat Exposure Journey
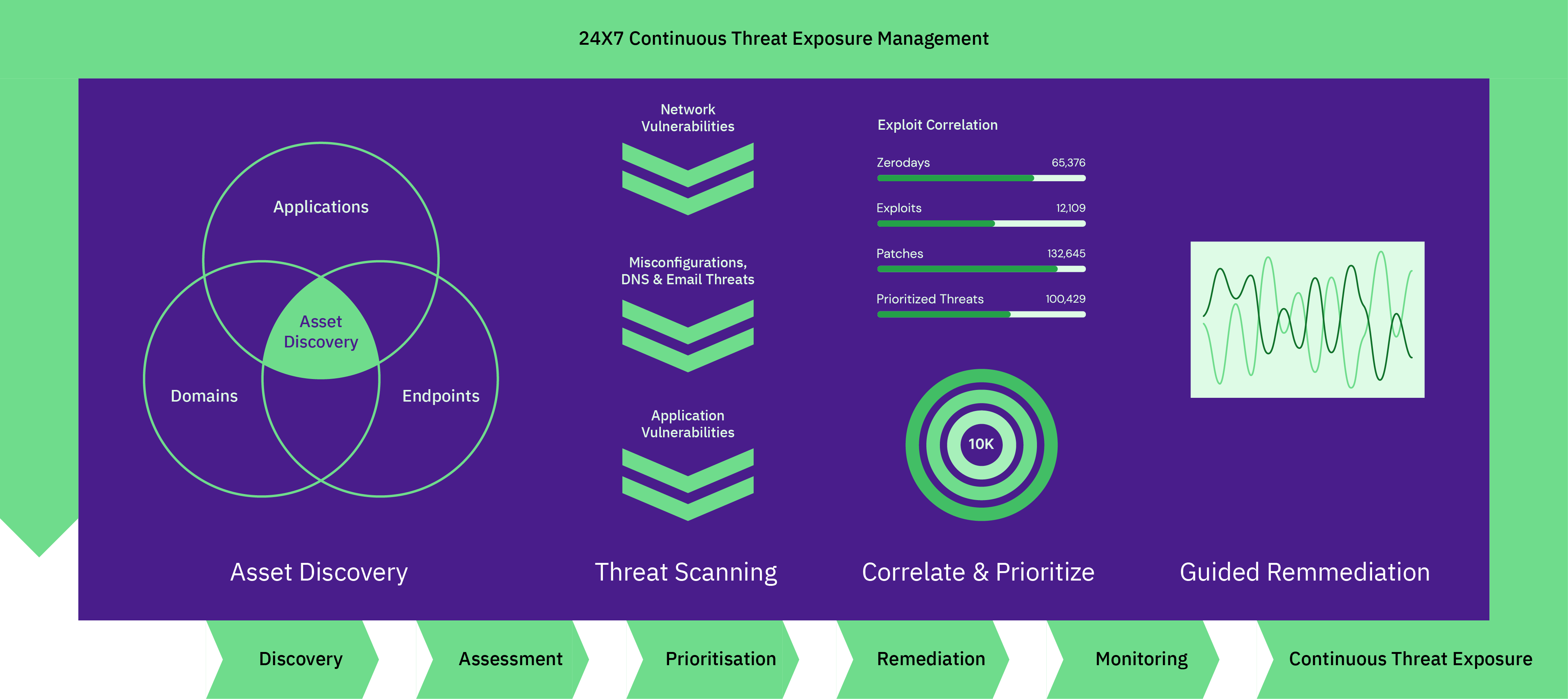
Asset discovery & management at scale
Discover Assets At Scale
Rapidly identify and catalog every digital asset across your enterprise, ensuring comprehensive oversight and a complete security view.
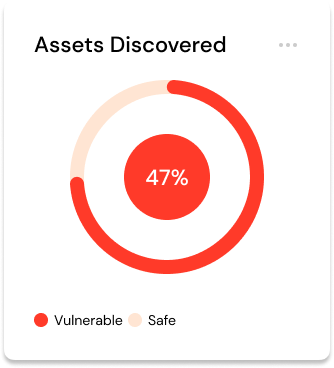
Identify Crown Jewels
Pinpoint your organization’s most valuable digital assets, enabling a targeted and priority-driven approach to security and risk management.
Integrate With CMDB & Cloud Providers
Seamlessly amalgamate data from Configuration Management Databases and cloud solutions, offering a unified and up-to-date asset repository.
Vulnerability Scanning & Management
Scan For Mis-configurations & Vulnerabilities
Proactively detect potential security loopholes and weaknesses, minimizing the window of vulnerability and enhancing asset security.
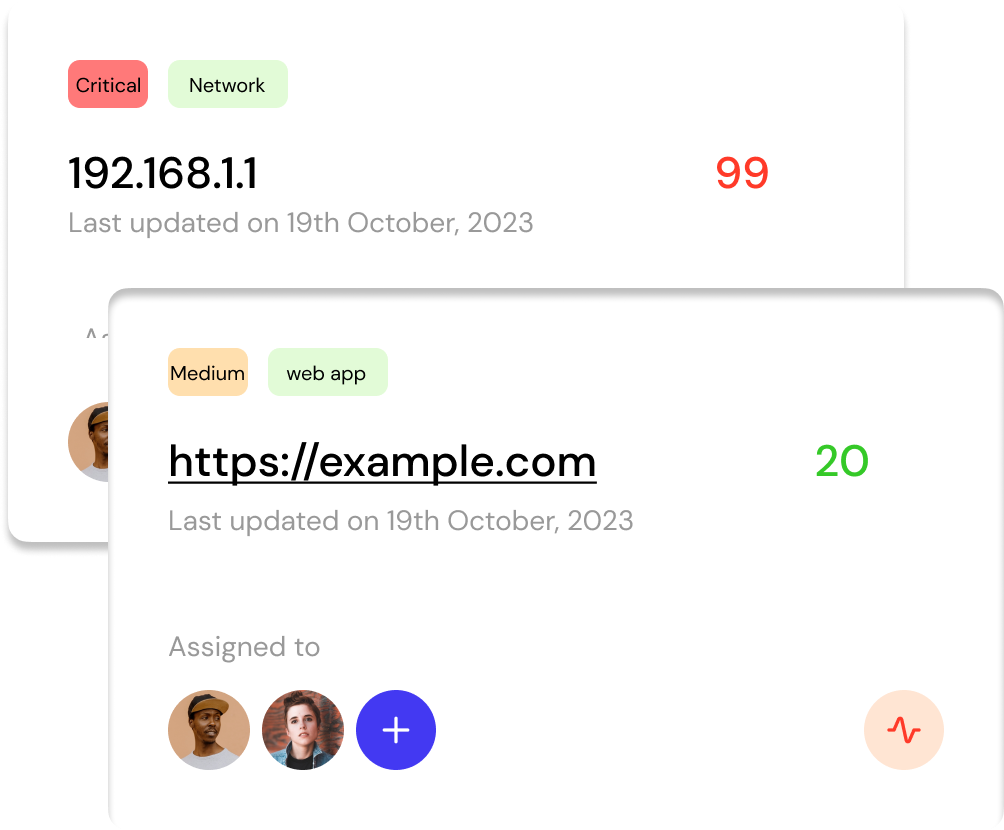
Aggregate All Vulnerabilities At One Place
Centralize vulnerability data, streamlining the review and mitigation processes, and fostering swift decision-making.
Use Advanced Filters To Speed Up VM Process By 10X
Efficiently sift through vulnerability data using intuitive filters, drastically accelerating the Vulnerability Management (VM) process.
Risk Based Prioritization
Use 3D Correlation To Prioritize Threats
Employ multi-dimensional analysis to evaluate and prioritize threats based on various factors, ensuring optimal resource allocation.
Get Guided Remediation On What To Fix First
Benefit from actionable insights that steer remediation efforts, ensuring effective and timely threat mitigation.
Integration Capabilities
Integrate With Top Most Vulnerability Scanners
Enhance your security landscape by seamlessly connecting with leading commercial scanning solutions, ensuring vulnerability aggregation.

Send Vulnerabilities To Ticketing Platforms
Ability To Create Customized Dashboards
Craft dashboards tailored to specific roles or objectives, ensuring relevant and actionable insights for all stakeholders.
Integrate with Slack, MS Teams, Email, Outgoing Hooks and More.
Facilitate real-time alerts and communication through your preferred channels, enhancing collaboration and ensuring timely responses.